Auto Acking Tool That Auto Uploads From Flash Drive
A long time agone, nosotros reviewed some devices which should be in any hacker's toolbox. I of these devices was a USB Rubber Ducky — a device which resembles a regular USB flash drive. When connected to a calculator, it claims to exist a keyboard and quickly enters all its commands. Information technology's a pretty cool thing and very useful for pentests, just why pay 40 dollars or more if a regular USB flash drive can exist taught the aforementioned tricks?
![]()
Warning
Don't forget that making the described changes to your USB wink drive may non just void the device's warranty but may also kill it. Experiment at your own run a risk!
Introduction
Last yr'due south Blackness Hat was full of many interesting reports. One of the nearly discussed was a report on the fatal vulnerability of USB devices, which allows regular USB flash drives to be turned into a tool for spreading malware. The attack was called BadUSB, simply subsequently jokes appeared on the Cyberspace referring to USBola, comparing this assault to the well-known virus.
Similar ideas for using HID devices for malicious purposes have been effectually for a while. It's a sin non to use the fact that the Os trusts devices connected to a USB interface. If we search the magazine's athenaeum, nosotros can discover an article on a similar topic describing the technique of using a special Teensy device to control a PC running Windows 7 (really, with any OS). The device bearded itself every bit a regular USB flash drive. All this suggested that the same trick could too be played with flash drives.
Prerequisites
A USB is a really universal interface. Just think how many devices we connect it to and how many devices it works with! Mouses, keyboards, printers, scanners, gamepads, modems, admission points, web cameras, telephones, etc. Without thinking, we plug the USB into the socket and the Bone automatically determines the type of device and loads the required drivers.
But how does it do it?
How wink drives work
In fact, the OS knows nothing about the continued device. Information technology has to wait until the device tells it what kind information technology is. Let's consider a uncomplicated example. When we plug a USB flash bulldoze into a USB socket, the wink drive informs the operating system of its blazon and volume. Information technology is worth remembering our shrewd Chinese colleagues, who learned how to produce higher capacity wink drives (some most ii TB). To figure out how this is possible, let'south remember (or learn) how the OS recognizes USB devices.
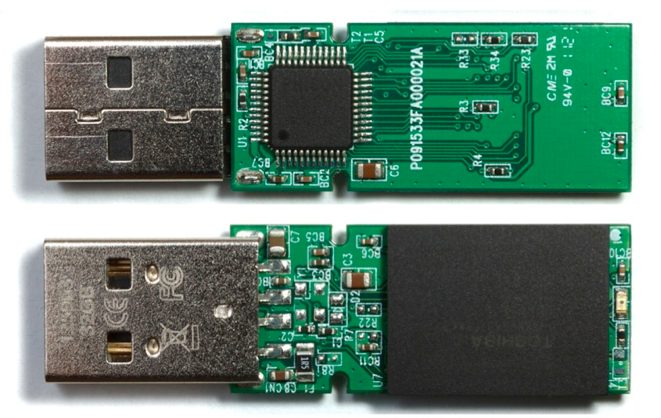
A USB flash bulldoze without its pretty case
USB device initialization algorithm
The purpose of USB devices is defined by course codes communicated to the USB host for installation of the necessary drivers. The class codes allow the host to work with unmarried-type devices from different manufacturers. The device may support one or several classes, the number of which is determined by the number of USB endpoints. When connected, the host requests a range of standard details from the devices (descriptors), which it uses to decide on how to work with information technology. The descriptors contain information about the manufacturer and device type, which the host uses to select the program commuter.
A regular USB flash drive will have class code 08h (Mass Storage Device — MSD), while a spider web camera equipped with a microphone will take two codes: 01h (Audio) and 0Eh (Video Device Class).
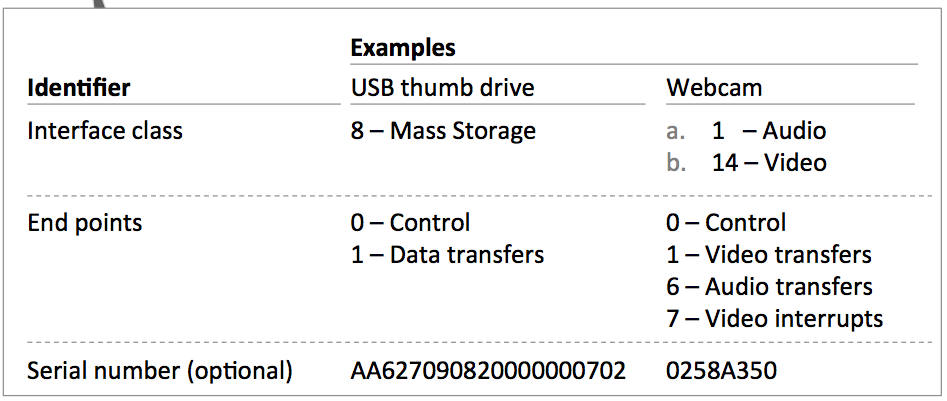
Device classes
When connected, the USB device is registered, receives an address and sends its descriptor/descriptors to permit the Os to install the necessary drivers and transport back the required configuration. After that, the host immediately starts working with the device. Once the work is completed, the device is de-registered. It is important to note that the devices may have several descriptors, they can also de-register and register as a different device.
If you open up the torso of a USB flash bulldoze, in add-on to the mass storage visible to the user, in that location is a controller responsible for the above-described actions.

The simply role of the device visible to the user
Bad USB or some history
At the final year'southward Black Hat conference, 2 researchers (Karsten Nohl and Jakob Lell) shared their experience on how to install a personal upgrade to the firmware of the USB flash drive controller. After a while, this USB wink drive was registered as a keyboard and entered the selected commands. Due to the serious nature of the problem, the guys decided not to make the code for this available. However, before long after, ii other researchers (Adam Caudill and Brandon Wilson) presented to the whole globe at Derbycon conference an operable PoC tailored to Phison 2251-03 microcontroller The code is available at GitHub.
Transformation
As you might accept guessed, today we will try to turn a regular USB flash drive into a pentester's cloak-and-dagger weapon!
First of all, we volition need a suitable device. As the lawmaking has been uploaded for the specific microcontroller only, we have two options — either discover a USB wink bulldoze managed by this controller, or perform some very challenging work researching and upgrading the firmware of another microcontroller. This time, we volition select an easier fashion and try to find a suitable USB flash bulldoze (hither is the list of vulnerable equipment). The controller is quite popular, so, miraculously, I plant a suitable USB flash drive amidst the dozen I have at home.
Starting the magic
Having found the suitable device (which we won't miss if it fails), we can start its transformation. First of all, we need to download the sources which the guys fabricated bachelor. Actually, the content is described in detail on their official wiki folio, but, just in instance, I will remind you what they take uploaded to GitHub:
- DriveCom — an app for communicating with Phison USB flash drives;
- EmbedPayload — an app for embedding Rubber Ducky inject.bin central scripts into custom firmware for subsequent execution when the USB flash drive is connected;
- Injector — an app that extracts addresses from the firmware and embeds the patching code in the firmware;
- firmware — custom 8051 firmware written in C;
- patch — drove of 8051 patches written in C.
![]()
INFO
When you employ Ducky scripts, you lot should recollect that the Delay command, which performs a filibuster for a set number of milliseconds, will work a footling differently on the USB flash drive than on Rubber Ducky, so you will take to suit the delay time.
Preparing the system
Having downloaded the archive with sources from GitHub, you will find that most of them take been written in C# and require compilation, and then you will need a studio. Another tool you will need is the Minor Device C Compiler, or SDCC. Install it in C:\Program Files\SDCC, you will need it to compile firmware and patches.
Having compiled all the tools contained in the annal, cheque again if this USB flash drive is suitable for firmware upgrade:
DriveCom.exe /drive=F /action=GetInfo where F is the alphabetic character of the bulldoze.
Getting the burner paradigm
The adjacent of import step is to select an appropriate burner image (8051 binary file, responsible for dumping activities and uploading firmware to the device). They are typically named:
BNxxVyyyz.BIN where 20 is the controller version (for case, for PS2251-03 it will be 03), yyy is version number (not important), and z reflects the retention page size and can look like:
- 2KM — for 2K NAND fries;
- 4KM — for 4K NAND fries;
- M — for 8K NAND chips.
You lot tin can expect for a suitable burner epitome for your USB wink drive here.
Dumping the original firmware
Before commencing your dirty experiments which could kill the USB flash drive, information technology is strongly recommended to dump the original firmware, so that if something goes wrong you can try to recover the device. First, switch the device to kicking mode:
tools\DriveCom.exe /drive=F /action=SetBootMode And so, use the DriveCom utility, passing the drive letter of the alphabet, the path to the burner image, and the path to the file where the original dumped firmware will be saved. It will look like this:
tools\DriveCom.exe /drive=F /action=DumpFirmware /burner=BN03V104M.BIN /firmware=fw.bin If you have done everything correctly, the source firmware will be saved to the fw.bin file.
![]()
World wide web
To check what controller is installed on the USB flash drive, you lot tin can use the utility usbflashinfo.
Preparing the payload
At present it's time to think virtually the functions we want our USB wink drive to take. Teensy has a separate Kautilya toolkit, which can be used to automatically create payloads. For USB Rubber Ducky, there is a whole website, with a friendly interface, which lets yous create any scripts for your device online. This is in addition to the list of finished scripts, which are available on the project's GitHub. Fortunately, Ducky scripts may be converted into binary to embed them and then into firmware. To do this, we volition need a utility Duck Encoder.
As for the scripts, there are several options:
- y'all can write the required script yourself, as the used syntax is like shooting fish in a barrel to chief (encounter the projection's official website);
- use finished ones uploaded to GitHub. Equally they have a reverse crush and other goodies — you will but accept to make minor corrections and convert them into binary course;
- or utilise the above-mentioned website, which will lead you step-by-step through all the settings and will allow you download the finished script in the grade of a Ducky script (or already in converted binary grade).
To catechumen the script into binary, execute the post-obit command:
java -jar duckencoder.java -i keys.txt -o inject.bin where keys.txt is a Ducky script, and inject.bin is the source binary file.
Flashing the firmware
Equally presently as nosotros accept the finished payload, information technology'south fourth dimension to embed information technology into the firmware. This is washed with the following two commands:
copy CFW.bin hid.bin tools\EmbedPayload.exe inject.bin hid.bin Please note that the firmware is first copied to hid.bin, and but and so is it flashed. This is because the payload tin can only be embedded into the firmware once, so the original CFW.bin must be left untouched.
Later on this manipulation, nosotros will take a hid.bin custom firmware file with an embedded payload. Yous will only have to identify the obtained firmware in the wink drive:
tools\DriveCom.exe /bulldoze=F /activeness=SendFirmware /burner=BN03V104M.BIN /firmware=hid.bin where F is the drive letter.
Alternative options
In addition to using the HID nature of the USB flash drive and turning it into a keyboard which types our payloads, there are another tricks that can be washed. For instance, you tin create a subconscious partition on the device, decreasing the space seen past the OS. To do this, you will first need to determine the number of logical blocks on the device:
tools\DriveCom.exe /drive=Due east /action=GetNumLBAs Then find the base.c file in the patch folder, uncomment the line #define FEATURE_EXPOSE_HIDDEN_PARTITION and add another directive — ascertain, which sets a new LBA number: #define NUM_LBAS 0xE6C980UL (this number must be fifty-fifty, so if y'all got, say, 0xE6C981 at the previous pace, you can subtract the number to 0xE6C940, for example).
Having edited the sources, you lot need to place the firmware which you lot want to patch into the patch folder, proper name information technology fw.bin and run build.bat, which will create a modified fw.bin file in patch\bin\. You can now flash this to the USB flash drive.
The options Password Patch and No Boot Mode Patch are washed in the aforementioned way; you can read more virtually them on the project's GitHub. My primary goal was to teach the USB flash drive to perform pre-fix actions, which we accept accomplished.
Issue
We accept reached our goal. Moreover, I promise you now empathize that USB flash drives (and other USB devices) tin no longer be seen simply every bit a drive that stores your information. In fact, it is almost a calculator, which can be taught to execute specific tasks. Although, PoC has so far simply been made available for a specific controller, you can exist certain that, every bit you lot are reading this article, someone is definitely working on others.
So, be careful when you plug in a USB device and proceed your optics open.
HINT
If the experiments have gone wrong and the USB flash drive behaves in a weird way, you can try to bring it back to life by manually switching it into boot mode and using the utility to restore the original firmware. To do this, earlier you connect information technology, you need to close contacts 1 and 2 (sometimes 2 and 3) of the controller, which are located diagonally from the point (run into image). Then y'all can try to bring the device back to life past using the official utility MPAL
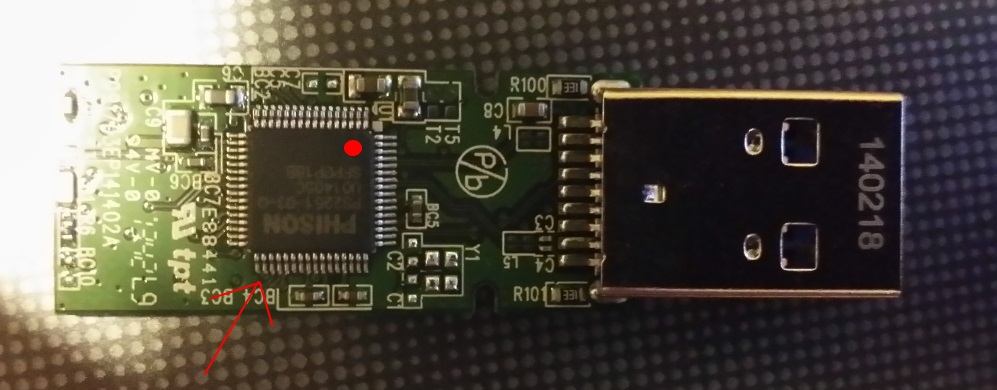
Switching a USB flash drive into kicking fashion past closing the shown contacts
Source: https://hackmag.com/security/rubber-ducky/
0 Response to "Auto Acking Tool That Auto Uploads From Flash Drive"
Post a Comment